As many of you know, I am a strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you would never be a hacker / pentesters of technology.
On the other hand, there are many here who come to Here who do not have the time or inclination to study Linux in order to earn a living. They want complex hacks / exploits, but they want to do it on Windows or Mac platforms. Although Metasploit will work on any of these platforms, it does not work well. Many of its capabilities do not work on, for example, the Windows platform.
Don't Miss: Hack any Android with IP Address Phonesploit
There are some excellent hacking / painting apps that work well in Windows, such as Cain and Abel, Wikto, and FOCA, but a new hacking framework called Exploit Pack has emerged.
The Exploit Pack, created by Juan Sacco, is similar to Metasploit but written in Java. Apart from the ubiquitous and easy-to-use GUI, Exploit Pack allows you to develop exploits in the language of your choice (Metasploit exploits must be written in Ruby). We will check that later.
Exploit Pack is open source and released under the GPL license. Its free version has over 350 exploits, while its Pro program has nearly 35,000 uses. Although we will be using the free program here, the Pro plan costs 300 Euros (about $ 320 USD). As the exploits move, that is less expensive.
It is my hope that by showing some of these hacks with Windows tools, those newbies will get a taste of the possibilities and be inspired to continue on Null Byte to learn Linux and its tools and capabilities. This is because Linux is the only operating system I can use as a professional plug, but for now - let's test and use the Exploit Pack!
Step 1: Download & Install Java
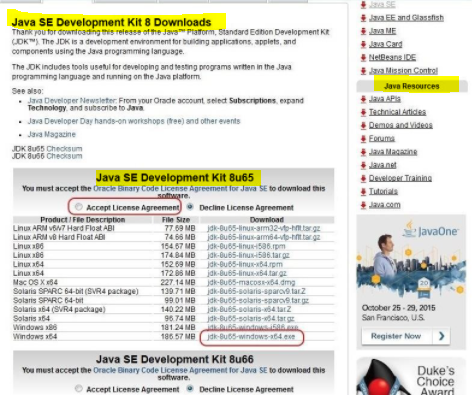
The first step, in fact, is to download and install the Exploit Pack. As I said above, it is written in Java, so you need to install Java 8. You can go to the Oracle website and download Java 8 for your build. Since I will be working on a 64-bit Windows 7 system, I have downloaded Windows x64 Java, as illustrated in the image below.
Of course, if you are using a different art, be sure to download specific Java for your architecture. Please note that before downloading it, you must accept the license agreement, and you need to have a free account with Oracle, too.
Next, keep installing Java on your system after downloading it.
Step 2: Download and install the Exploit Pack
Now, we can download and install the Exploit Pack on the Exploit Pack website. Note that the MD5 hash is close to each download. It is a good practice to check to see if the MD5 of the downloaded code is the same as the MD5 to make sure that the code is not corrupted or altered in any other way.
For those who want to use Exploit Pack with Kali Linux as a VMware server, note that Exploit Pack is also available with Kali 2.0 as a VMware image (the final download option).
Step 3: Start the Exploit Pack
When you have finished downloading the Exploit Pack, go to the directory you have installed. Personally, I created a directory called "Exploit Pack" and pulled everything out there.
If you go to the directory with the Exploit Pack, check the usable .jar file as I circled above. Click on it and it will start opening the Exploit Pack.
Click on "Continue" when you see this screen click to open the Exploit Pack GUI.
Step 4: Exploit Pack GUI
When the Exploit Pack is done, you should be greeted by a friendly GUI like the one below. For those who are more comfortable with "point and click" than the Linux command line, you should find that this interface is accurate and standard, I hope.
Step 5: Check the Interface
Exploit Pack has a clean and easy-to-use interface. As you can see, if you go to the far left window, we can see three tabs, Exploits, Auxiliary and Target. When we click on Exploits, it displays a long list of exploitation categories, which are separated mainly by the application used (although there are other non-OS categories such as cgi, etc.).
If we scroll down that list a bit, we will find Windows exploits. Click and expand that list and expose the long list of Windows exploits we can use to hack Windows programs. We will use some of those in future lessons.
We can click on the "Auxiliary" tab and - like Metasploit - it contains Scanner and DoS modules.
We can search for modules by going to the "Module Search" box under the Exploit window, as shown below.
In the Module Search window, we may choose to display functionality, latest, or all, as well as search by name, author, or platform.
Don't Miss: How to Know phone is Hacked or Not
Now that we have installed and have a basic understanding of the Exploit Pack, come back to explore how you can use it to get into any kind of program!


















0 Comments