Sorry. It's Bruteforce too.
If you have seen my tutorial on getting Instagram hack account passwords, there have been many complaints that the script was not working properly. Of course, that wasn't my text, so I decided to make my own instead.
Don't Miss: How to Hack online Passwords with THC Hydra & Temper Data
After a long time, I introduce you, Faitagram.
Still enough to say, Let's get right into the lesson.
Step 1: Getting Ready !
By the way, Faitagram stands for Fa(cebook) (tw)it (ter) (inst)agram.
To compile a script, all you need to type in the forum is:
git clone https://github.com/Juniorn1003/Faitagram.git/
Creating a Faitagram script.
After cloning, type "ls" to see the contents of the folder.
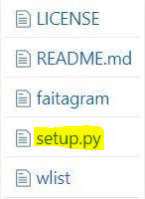
After typing that, you'll see 5 things:
License, Readme, faitagram, setup.py and wlist.
The license is just a MIT license, Readme has details about the script in it, faitagram is the main source, setup.py is the input dependent, and the wlist is wordlist.
Do you have that? Now lets chmod files so we can access them.
chmod + x faitagram && chmod + x setup.py
We've done that, including all the requirements for using the script by typing:
python setup.py
It will cover a whole lot of stuff.
You just need to wait.
After the installation is complete, there are instructions for each Facebook, Twitter, Instagram.
The faitagram file contains a strong password list, so don't worry about the list of words.
But if you still want to test it, instead of using your own word list.
The format is:
Python faitagram -s service -u username -w wordlist -d delay
In the service, instead on facebook, twitter or instagram.
Username of target username.
a list of words is the path to a list.
the delay can be selected, and it means that the seconds delay will fall asleep while trying to passwords.
delay error is 1 second.
There are 3 ways, choose one and follow me.
-FaceBook-
To start bruteforcing on Facebook, all you need to type is:
Python faitagram -s facebook -u (email) -w (word list) -d (delay)
Category (email), for which email is addressed.
Category (of word for word) route to the list of words.
And (delay) the delay (seconds).
Delay can be selected, just do not type "-d" If you do not want to use it.
But, something else is worth it.
If you do not have a list of words, type "wlist" instead of (wordlist).
Only on Facebook, it will ask you to enter the target name.
It simply prevents errors, and checks the username.
Here are some examples of command:
python -s facebook -u HackersField -w list -d 3
python -s facebook -u Hacker -w /root/password.txt
Python -s facebook -u Bhat Aasim -w /root/SadminDontBanMe.txt -d 2
-Twitter-
To start forcing on Twitter, you need to type:
Python faitagram -s twitter -u (username) -w (word list) -d (delay)
-S stands for services, -u username, -w for route to wordlist -d delay (seconds).
So all you have to do is enter the target username in the (username) section,
the path to the list in the section (worslist). That should be, but -d can be selected.
Just do not enter the -d parameter if you do not want to use it.
Like:
Python faitagram -s twitter -u Victim -w list
After that the system will automatically set the delay to 1 second.
-Intagram-
To start bruteforcing on Instagram, what you need to type:
Python faitagram -s instagram -u username -w wordlist -d delay
In the username, change it to the target username, in the list, change it to the list of names.
With a delay, it is optional, you don't really need it, but change it at intervals to be between the bruteforcing passwords.
Don't Miss: How to Hack WIFI Passwords with Evil Twin 2020
If you do not want to delay, just do not type parameter -d.
How does this work
This text is made entirely of python.
It will never fail, because it uses selenium to do it.
selenium is a program for using the real web and making the script do everything else, but I decided to make it work on the visual display, using Xvfb and pyvirtualdisplay.
There may be errors, and the only thing you should expect while using bruteforcing.
This document uses STEM for the Proxy.
I think it all comes from me, Thank you for reading.








0 Comments