Over the years, we have explored a number of ways to have the system, exploited, or corrupted the system. On the other hand, we did not spend much time on the denial of service (DoS) attacks.
For those of you who are new here, denial of service is basically a simple attack that keeps the targeted system running smoothly. In simple terms, it uses all the resources of the system so that others cannot connect. Sophisticated attacks will cause the system to crash or create an endless loop using all system CPU cycles.
In general, DoS attacks are a simple and complex method of attack. Some have even said that an eight-year-old child could take part in a DoS attack, and there is truth in that statement because some tools make it as easy as entering an IP address and hitting "Start."
In recent years, DoS and DDoS attacks (this includes more than one source of attacks) have been growing rapidly and many companies / websites are using special anti-DoS tools and techniques (among the most popular and expensive by Incapsula).
Don't Miss: How to Create Smartphone Hacking Lab
In this article, I want to lay the groundwork for DoSing strategies and give you some tools for doing so. Before I do that, though, I want to point out that some of the tools we've tested here at Null Byte are useful for DoS attacks, including Hping, Nmap, Metasploit, and Aircrack-ng (for wireless DoSing points).
Methods
You can classify refusal attacks on at least three different types of services, including:
- Volume-Based
This is a very simple attack. The attacker simply sends a large number of packets to the target thus using all the resources. The devices used can simply be bandwidth. These attacks include ICMP and UDP floods.
- Based on Protocol
These attacks typically use server resources rather than bandwidth on or off server. They can also use network equipment resources on the server side (such as fire logs, access systems, and switches). Examples include Smurf attacks (ICMP on broadcast IP with corrupted IP), Fraggle attacks (similar to Smurf, using only UDP), SYN floods, dead ping (large ICMP with the same location as the source (IP and port), and many others.
- Application Layer Attack
These attacks are compromised by what appear to be legitimate domain applications (layer 7) on a server that intends to crash. This includes attacks on Apache HTTP Server and Microsoft IIS, and includes tools like Slowloris.
DoS & DDoS tools
There are literally hundreds of DoS and DDoS tools available. Within Kali, we can find helpful modules within Metasploit specifically for DoSing. When we navigate to:
kali> cd/usr/share/metasplot-framework/auuxiliary/dos
And a list of content for this indicator, we see that Metasploit has organized its DoS tools by target type. There are hundreds of tools for refusing to work in Metasploit.
We can also find hundreds of DoS tools in the Exploit Database built in Kali, and more on Exploit-DB.com. We can find the list of Exploit-DB DoS tools by navigating to:
kali>/usr/share/exploitdb/platforms/windows/dos
The long list (ls -l) of this directory lists all Windows DoS tools. The same, shorter list is /usr/share/exploitdb/platforms/Linux/dos.
Some Popular DoS Tools
There is no way I can write and review all the DoS tools, but here is a short list of the most popular and effective ones. This is far from a complete list, but I hope to give you the basics on some of the most popular DoS and DDoS tools. If you have a favorite, by all means, please comment on the download link.
Don't Miss: Turn any Windows into a Hacking Machine
One quick warning note: Be careful when looking online for DoS or DDoS tools. Most of them simply take you to a bad link and install Trojan on your system. I don't know anyone who can do that. ;-)
1 LOIC
Low Orbit Ion Cannon (LOIC) could be the most popular DoS tool and has a Hacker lore. It is able to send large amounts of ICMP or UDP packets to the target, thus completing the bandwidth, and has been used in some of the most effective and well-known DoS attacks.
LOIC was successfully used by 4chan in a Project Chanology attack on the Church of Scientology website in 2009, and Anonymous in Operation Payback attacks against PayPal, Visa, and MasterCard to retaliate by cutting off WikiLeaks donations.
LOIC attacks can be significantly reduced by reducing UDP and ICMP packets and limiting how many packets can be sent and delivered to any single client. You can download LOIC from SourceForge. This tool is based on Windows and is as simple as pointing and clicking.
2 HOIC
HOIC was founded during Operation Payback by Praetox - the same people who founded LOIC. The main difference is that HOIC uses HTTP flood using support files that allow a small number of users to use the DoS website effectively by sending a flood of HTTP GET applications and random mail. Can do DoSing simultaneously on 256 domains. You can download it from SourceForge.
3 XOIC
XOIC is another easy-to-use DoS tool. The user simply needs to set the IP address and the target port, select the protocol (HTTP, UDP, ICMP, or TCP), and start shooting! You can download it from SourceForge
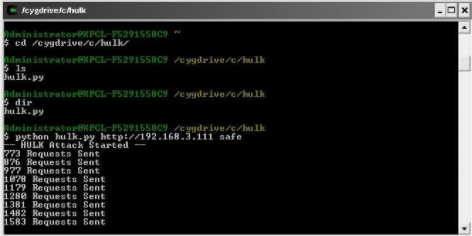
4 HULK
Unbearable HTTP Load, or HULK, is another tool that can slow down web servers. This tool uses a variety of obfuscation techniques to limit identified strength to reduce attacks. You can download it from Packet Storm.
5 UDP Flood
UDP Flooder does as you might expect - sending a flood of UDP packets to the target. It has been used successfully to exclude players from their networks (online games primarily use UDP). You can download it from SourceForge.
6 RUDY
R-U Dead-Yet, or RUDY, takes a different approach to DoSing websites. Enables the user to select a form from a web application and use that form to send a flood of POST requests. You can download it from Hybrid Security.
7 ToR Hammer
ToR's Hammer is designed to be operated by the ToR network to make their name anonymous and limited to reduction. The problem with this strategy is that the ToR network tends to slow down, thus reducing the rate at which packets can be sent and thus reducing the performance of this tool. You can download it from Packet Storm or SourceForge.
8 Pyloris
Pyloris is another DoS tool, but with a different strategy. Allows the user to create their own unique HTTP request titles. Then try to keep this TCP opening open for as long as possible to complete the connection line. If it does this, no official communication can be made and new attempts to connect with other users will be downgraded. You can download it from SourceForge.
9 OWASP switchblade
The Open Web Application Security Project (OWASP) and ProactiveRISK have developed a switchShlade DoS tool that will be used to test the performance of a web application in DoS efforts. It has three modes, 1. SSL Half-Open, 2. HTTP Post, and 3. Slowloris. You can download it from OWASP.
10 DAVOSET
DAVOSET (DDoS attacks by other site-building tools) is a DDoS tool, written in Perl, that uses zombie programs to spread attacks across multiple programs. This tool uses Risk of Business and XML's external business risk on other sites to "zombie" and attack the targeted site. Includes over 160 zombie services. You can download it from Packet Storm or GitHub.
11 GoldenEye HTTP DoS Tool
GoldenEye is a simple DoS tool that loads an HTTP server that tries to end its resource pool. It’s good to test your website, but it doesn’t really work in the real world as most perimeter protections will get you. You can download it from GitHub.
12 THC-SSL-DOS
This DDoS tool (built in Kali) is different from most DoS tools in that it does not require a large amount of bandwidth and can be run on a single system. Attacks being compromised on SSL to slow down the server. You can download it from THC, but if you use Kali, you already have it.
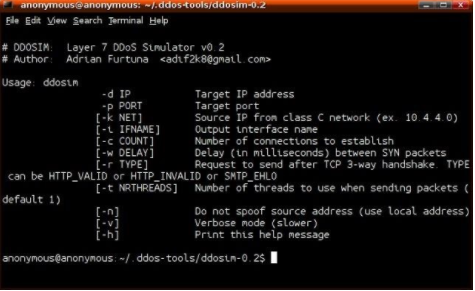
13 DDOSIM - Layer 7 DDoS Simulator
This tool from Storm Security mimics DDoS attacks from various Zombies with random IP addresses. Trying to create a complete TCP connection (SYN-SYN / ACK-ACK). As the name implies, it works in the program layer (layer 7). It can also mimic DDoS attacks on an SMTP server and flood TCP on random ports. You can download it from SourceForge.
Keep coming back, my budding hackers, as we continue to explore the tools and techniques of the most important skill of the future - hacking!























0 Comments