Welcome!
Mr. Robot's episode 6 came and went and, as usual, didn't disappoint. Once again, our hero, Elliot, has used his ingenuity and hacking skills to scare and inspire us.
In this episode, Elliot is mistreated by a cruel and relentless drug dealer, Vera, to get her out of jail. He grabbed Elliot's new love interest, Shayla, kidnapped her and gave Elliot until midnight to attack the prison computer system to free her.
Elliot tries to explain to Vera that such scams cannot be committed in a matter of hours, but rather days or weeks to detect security threats. Vera, as an aggressive and fragile killer, will not agree to give Elliot more time. Because of this, Elliot has to try other less-than-ideal methods to try to get Vera out of prison to save the lovely Shayla (as you remember, Shayla is also her morphine supplier).
Malicious Flash Drive
In his first attempt to hack the prison, Elliot has Darlene, a friend and a meses from the f / community, "accidentally" cut off the flash drives that go outside the prison. The strategy here is that if someone inside the prison network picks up one and puts it into a computer program, it will then install malware and give Elliot external connections.
As expected, the reduced repair officer selects it and installs it on his computer. Elliot is able to find SSH connections on it, but before he can do anything, AV software finds it and disconnects Elliot. Elliot then criticizes Darlene as a "script-kiddie" for using known malware from Rapid9 (a reference to developer Metasploit, Rapid7) instead of developing a new exploitation, and Darlene defends herself by saying "I only have one hour." (You may have re-installed it with Veil-Evasion and may have passed AV software not available.)
Don't Miss: Hack any Windows With an Image ? Windows XP/7/8/10 Hacking
Some have asked if this approach could work. Before disabling the default autorun feature in today's operating systems, you may have an EXE file on the flash drive that would run automatically. In the current OS, autorun is automatically disabled.
We can assume that this device has an autorun feature enabled or, possibly, Darlene installed malware on a redesigned flash drive to mimic the USB keyboard. When a flash drive is installed in the system, the operating system recognizes the flash drive as a USB keyboard, gives it access to the login user's login and inserts its malicious code into the application. Therefore, this method might have worked if Darlene had rewritten the malware via Veil-Evasion.
While Elliot is visiting Vera in prison, she is carrying her phone, where she has installed a Wi-Fi scanning app. With that scanner, he can see all the Wireless APs and see that they are all protected by WPA2. Although he knows he can break into WPA2, he realizes that the short time he worked with him is not enough to force WPA2.
While scanning wireless devices and encryption technology with his phone, Elliot sees a Bluetooth connection when a repair officer's car drives next to him.
That puts Elliot in a new strategy, that is, hacking Bluetooth and installing a computer system in prison via a prison cell car cell phone connection!
Hacking a Bluetooth keyboard !
Elliot's strategy here is to connect the Bluetooth connection of a police car to his keyboard. If he can make a laptop believe that his keyboard is actually a police keyboard, he can control a police laptop and get inside the prison network. Once inside the network, they can download malware to control digital-controlled prison systems.
Step 1: Enable Bluetooth
Before Elliot can do anything, you need to enable Bluetooth on his Linux hacking program by starting the bluetooth app:
kali> bluetooth service start
Next, you need to activate the Bluetooth device:
kali> hciconfig hci0 up
You then check to see if it really works, and its properties, by typing:
kali> hciconfig hci0
Please note "BD Address" in the second line - this is the MAC address of the Bluetooth device.
Step 2: Scan Bluetooth devices
The first thing Elliot did was to scan the Bluetooth connection. If you look closely at Elliot's screen, you can see that you are using hcitool, a built-in Bluetooth tool built into Kali Linux. While this works, I have had better success with btscanner, a built-in Bluetooth scanner with a basic GUI. To use, simple type:
kali> btscanner
Then select "I" to start scanning. You can see the results below.
Using btscanner, we can get a list of all Bluetooth devices in range. This one has a MAC address and the name of "Tyler" - to destroy this device, we must destroy the MAC address and device name.
Don't Miss: How to Hack Contacts, SMS, Call Logs, Location & More ? Hack Mobile Phone
This is how Elliot found the MAC address and the name of the Bluetooth device in the police car. Remember that Bluetooth is a low power protocol with a distance of about 10 meters (although it has a directional antenna, distances up to 100 meters are reached).
Step 3 : Spoof the MAC address of the keyboard
Now that Elliot has the name and MAC address of the police keyboard, you will need to disassemble it by assembling the police keyboard with this information. Kali Linux has a tool designed for extracting Bluetooth devices called spooftooph. We can use it to disable the keyboard with a command like this:
kali> spooftooph -i hci0 -a A0: 02: DC: 11: 4F: 85 -n Car537
- -i Sets the device, in this case hci0
- -a Specifies the MAC address we want to spend
- -n specifies the name of the device we want to disable, in this case "Car537"
If done properly, our Bluetooth device will damage the MAC address and the name of the police computer-Bluetooth device.
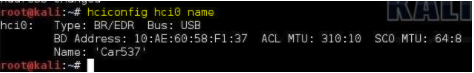
To check if we are successful, we can use the hciconfig followed by the device and change the "name" to list the device name. Remember, this is our Bluetooth device that we are trying to impersonate with the police car Bluetooth device. If successful, we will have the same MAC address as the police device Bluetooth name.
kali> name of hciconfig hci0
Now, we have a Bluetooth device which is a complete clone of the Bluetooth keyboard for a police car!
Step 4 : Connect the Bluetooth Device to Cop's Laptop
Now, this is where the truth and Mr. Robotstoryline split. Mr. Robot's hacking makes perfect sense, but even in this show, the director takes a certain writing license. That’s allowed - creative activities shouldn’t be limited to reality.
In order for Eliot to connect to a police car laptop, you will need a connecting key (this is the key to identify a pre-paired Bluetooth device) that is switched between the keyboard and the Bluetooth adapter on the laptop.
He can guess it (impossible) or break it, but it won't be as fast as it appears in this game. Another possibility is that when the system restarts or the keyboard is disconnected, Elliot may connect to the laptop as it is a police keyboard indicator. In any case, it will take more time than Elliot does in this episode of hacking a police Bluetooth keyboard.
Step 5: Hack The Prison
In the last step, Elliot uses a hacked police computer to install malware via FTP that will enable him to control the prison cell doors. Few people know that prisons and other industrial systems, commonly referred to as SCADA, are highly hackable
Don't Miss: Hack WIFI Password with Android Phone ? See Saved Wifi Passwords
The Stuxnet hacking of an uranium enrichment site in Iran was very similar to this. This industrial system consists of PLCs that are basically digital controllers. Apparently, the prison had PLCs that controlled the prison cell doors (reasonable assumptions) and Elliot's malware infected and empowered him, enabling him to open all the cells, freeing Vera and all the other prisoners.


















0 Comments